This tutorial will guide you through flashing a new IOS onto a or . Cisco devices use IOS images which
Continue reading
The thoughts and ramblings of an Engineer

This tutorial will guide you through flashing a new IOS onto a or . Cisco devices use IOS images which
Continue reading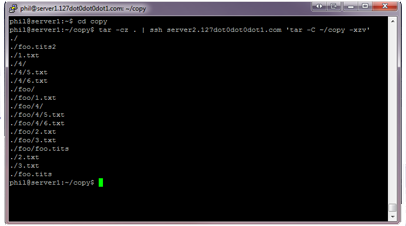
This is a really useful tip, and it has infinite uses in a *nix environment. You can pipe data over
Continue reading
It’s mighty dull but pretty tricky to find on the travesty that is the Council’s website. First you’ll need to
Continue reading
Tcpdump is a useful tool to capture network packets on a Linux, UNIX, BSD, etc. system. It is nice, however,
Continue reading
I get asked a lot about the shit under my stairs. It’s not particularly interesting, but I thought I should
Continue reading