Hetzner offer very well specified physical servers at extremely low prices. I’ve used them for many years and they’ve proved to be extremely reliable. With each server, Hetzner will give you a single IPv4 IP and a /64 IPv6 subnet. You can also run virtualization software such as Proxmox and it’s often desirable to run a firewall such as pfSense on a virtual machine to protect the other virtual machines.
All good in principal, but the /64 IPv6 subnet has caused some confusion. Surely you need some more address space to be able to route the /64 subnet? It turns out, no. Hetzner don’t use NDP or proper IPv6 routing… they seem to just deliver the address space to the server (probably via static NDP entries mapping your /64 to your server’s MAC address). This actually works to our advantage because you do not need to assign the physical server any IPv6 addresses in the issued /64.
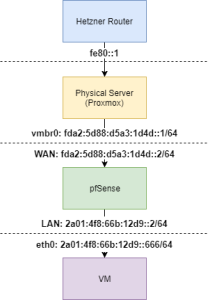
Broadly, the setup looks like this:
- Physical server does not have an IPv6 address assigned to its physical interface
- Physical server has IPv6 forwarding turned on
- Proxmox (thus the physical server) has a private IPv6 address assigned to the bridge (vmbr) interface that it shares with pfSense
- pfSense WAN interface has another private IPv6 address in the same subnet as the vmbr assigned to it
- pfSense “LAN” interface has an address from your public /64 assigned to it
- pfSense uses SLACC to assign IPs in your /64 to the VMs behind it
- Physical server has a route to your assigned /64, via the private IP you assigned to your pfSense WAN interface
- Physical server has a default IPv6 route to fe80::1
Here’s a picture where the assigned /64 is 2a01:4f8:66b:12d9::/64 and the private IPv6 /64 used between Proxmox and pfSense has been chosen fairly randomly using this:
Here’s the relevant parts of the network config on the physical Proxmox server:
iface vmbr0 inet static
address 10.69.69.1
netmask 255.255.255.240
ovs_type OVSBridge
post-up route -A inet6 add default gw fe80::1 dev enp0s31f6
post-up route -A inet6 add 2a01:4f8:66b:12d9::/64 gw fda2:5d88:d5a3:1d4d::2
post-up echo 1 > /proc/sys/net/ipv4/ip_forward
post-up echo 1 > /proc/sys/net/ipv6/conf/all/forwarding
iface vmbr0 inet6 static
address fda2:5d88:d5a3:1d4d::1
netmask 64
If you have any questions, leave a comment.




Hi,
can you post ip4 config?
Hi,
Do you still use this Setup ?
How did you configure the primary network interface of the Host ?
I do still use this setup and the methodology is sound. That said, I noticed the other day that a reboot of the host didn’t bring it all back up as intended. Not sure if that’s because of a Proxmox upgrade or other issue but v6 wasn’t routing properly across the host machine. Here’s the relevant bit of my network config but I can’t promise it’ll survive a reboot currently:
allow-ovs vmbr0iface vmbr0 inet static
address 10.69.69.1/28
ovs_type OVSBridge
post-up ip -6 addr add fda2:3333:d5a3:1c4c::1/64 dev vmbr0
post-up route -A inet6 add default gw fe80::1 dev enp0s31f6
post-up route -A inet6 add 2a01:4f8:10a:11c5::/64 gw fda2:3333:d5a3:1c4c::2
post-up echo 1 > /proc/sys/net/ipv4/ip_forward
post-up echo 1 > /proc/sys/net/ipv6/conf/all/forwarding
#Frontend WAN
Thanks for this advise. It’s nice to know, how to make IPv6 really usable on Hetzner!
It is possible to use the Linux bridge instead of OVSBridge in this setup. I can not use those two types on the same proxmox machine.
And one more: Can I redirect a subnet or ip (v6) to an external Host?
Sure – you can use a Linux Bridge rather than OVS. I’ve used OVS on all Proxmox hosts for a while now as it’s a lot more flexible but there’s nothing OVS specific here.
You can do multiple subnets. Just add a route per subnet 🙂
Hello!
Thank you for sharing your settings.
On the pfSense side is there an IPv6 gateway to setup on WAN ? I’m confused… would it be fda2:3333:d5a3:1c4c::1 ?
Also in my setup for now:
– ping fda2:3333:d5a3:1c4c::1 from pfSense = Ok
– ping fda2:3333:d5a3:1c4c::2 from Proxmox = KO… is this normal ?
Thanks again !
Most likely, yes. Are you allowing all inbound ICMPv6 traffic to pfSense? If not, you probably should be – blocking ICMP is a bad idea, especially in IPv6 world.
Thanks for your answer !
I finaly did the “additional IP” way and dedicated it to the pfSense (additional IPv4 and IPv6/64). Network configuration is so much simpler ^^
Hi,
I’ve been struggling with this for soo long,
I ordered an additional IP as well for use with pfSense.
In your comment you mentioned you dedicated ipv6 to pfSense, how did you do that?
Can you also share your config, thank you
The post should describe it in enough detail – the configs themselves are pretty large but the bits relating to IPv6 are minimal
Thank you very much for this article! That made my life much easier today! 🙂